How Podesta's Gmail Account Was Breached
Clinton campaign staff was duped by hackers
![]()
OCTOBER 28--So how did John Podesta’s e-mail account get hacked?
The answer to that question came into embarrassing focus this morning with the latest Wikileaks dump of correspondence stolen from the Gmail account of Hillary Clinton’s  campaign chairman.
campaign chairman.
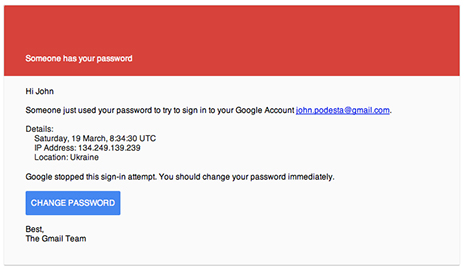
On March 19, a Saturday, Podesta received an e-mail--purportedly from Google--warning him that, “Someone has your password.” The alert (seen above) informed Podesta that a sign-in attempt from an IP address in Ukraine was thwarted and that, “You should change your password immediately.”
The e-mail, addressed "Hi John," included a blue “CHANGE PASSWORD” box to be clicked.
As TSG reported in August, similar messages were sent to the Gmail accounts of scores of other Clinton campaign officials around the time Podesta received the phony alert. An identical e-mail--containing the exact Ukrainian IP address--was received on March 22 by William Rinehart, a campaign organizer. The IP address included in the e-mails received by Podesta and Rinehart traces back to Kyivstar, Ukraine’s largest telecommunications company.
Like Rinehart, Podesta’s Gmail account was compromised by the “spear phishing” e-mail, which American investigators have concluded was  the work of Russian intelligence operatives.
the work of Russian intelligence operatives.
After the e-mail arrived in Podesta’s account, it appears that his chief of staff, Sara Latham, sought guidance from an IT worker with the Clinton campaign. After examining the “Someone has your password” e-mail, staffer Charles Delavan (seen at left) mistakenly assured Latham and Shane Hable, the campaign’s chief information officer, that, “This is a legitimate email. John needs to change his password immediately, and ensure that two-factor authorization is turned on his account.”
Delavan’s 9:54 AM e-mail included a link to an actual Google password change page. “It is absolutely imperative that this is done ASAP,” he added.
Latham then forwarded Delavan’s email to Podesta and campaign staffer Milia Fisher, who had access to Podesta’s Gmail account. “The gmail one  is real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out of his in box!”
is real,” wrote Latham, who instructed Fisher to change Podesta’s password since “Don’t want to lock him out of his in box!”
But instead of following the link provided by Delavan, it appears that Podesta or Fisher (pictured at right) clicked on the “CHANGE PASSWORD” box in the original “spear phishing” correspondence (a copy of which which was included in the e-mail chain that Saturday morning).
That link led to what appeared to be a legitimate Google page, but was actually a site designed by the hackers to capture a target’s log-in credentials. The link to the spoofed Gmail page included a lengthy underlying url with the .tk suffix, indicating that the domain created to trick Podesta was registered in Tokelau, a remote group of South Pacific atolls.
The hidden 293-character link included a string of characters containing the encoded Gmail address for Podesta (john.podesta@gmail.com).
The e-mails stolen in the Podesta hack and posted on Wikileaks show that the most recent correspondence is from March 21.
While Delavan protected his Twitter page following the publication of this story, he did offer the public some sage advice earlier this week. In an October 25 tweet, Delavan wrote, “don’t click on anything ever. delete your email account. move to the woods.” (1 page)